Private regional endpoints in Vespa Cloud

Photo by Taylor Vick on Unsplash
Vespa Cloud exposes application container clusters through public endpoints, by default. We’re happy to announce that we now also support private endpoints, in both AWS and GCP; that is, our users can connect to their Vespa application, in Vespa Cloud, exclusively through the private network of the cloud provider.
Why use private endpoints
Traffic to private, regional endpoints avoid the trip out onto the public internet, and both latency and costs are reduced:
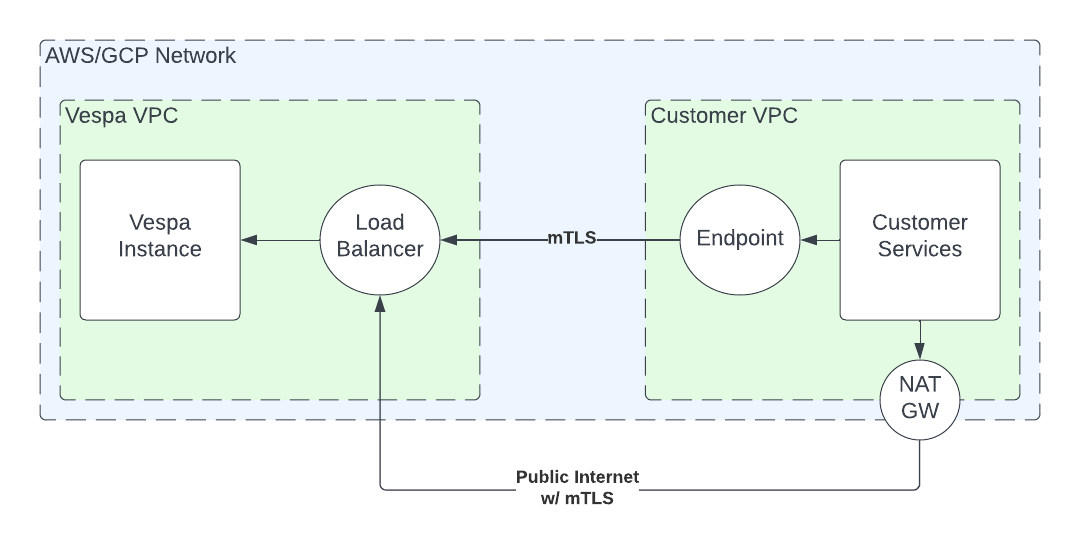
With private endpoints enabled, it is also possible to disable the public endpoints of the application, for another layer of access control and security.
How to set up private endpoints in Vespa Cloud
To use this feature, clients must be located within the same region (or availability zone) as the Vespa clusters they connect to. Configuring and connecting to the application is done in a few, simple steps:
- Configure and deploy a private endpoint service, optionally disabling the public endpoint as well.
- Set up a VPC endpoint in your AWS or GCP account, in the same region.
- Verify it all works.
Read more about AWS PrivateLink or GCP Private Service Connect for further details.